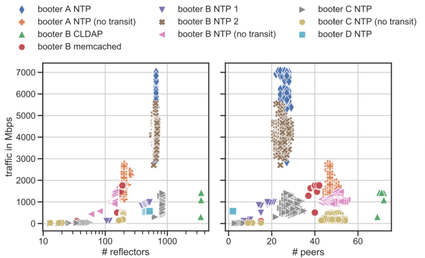
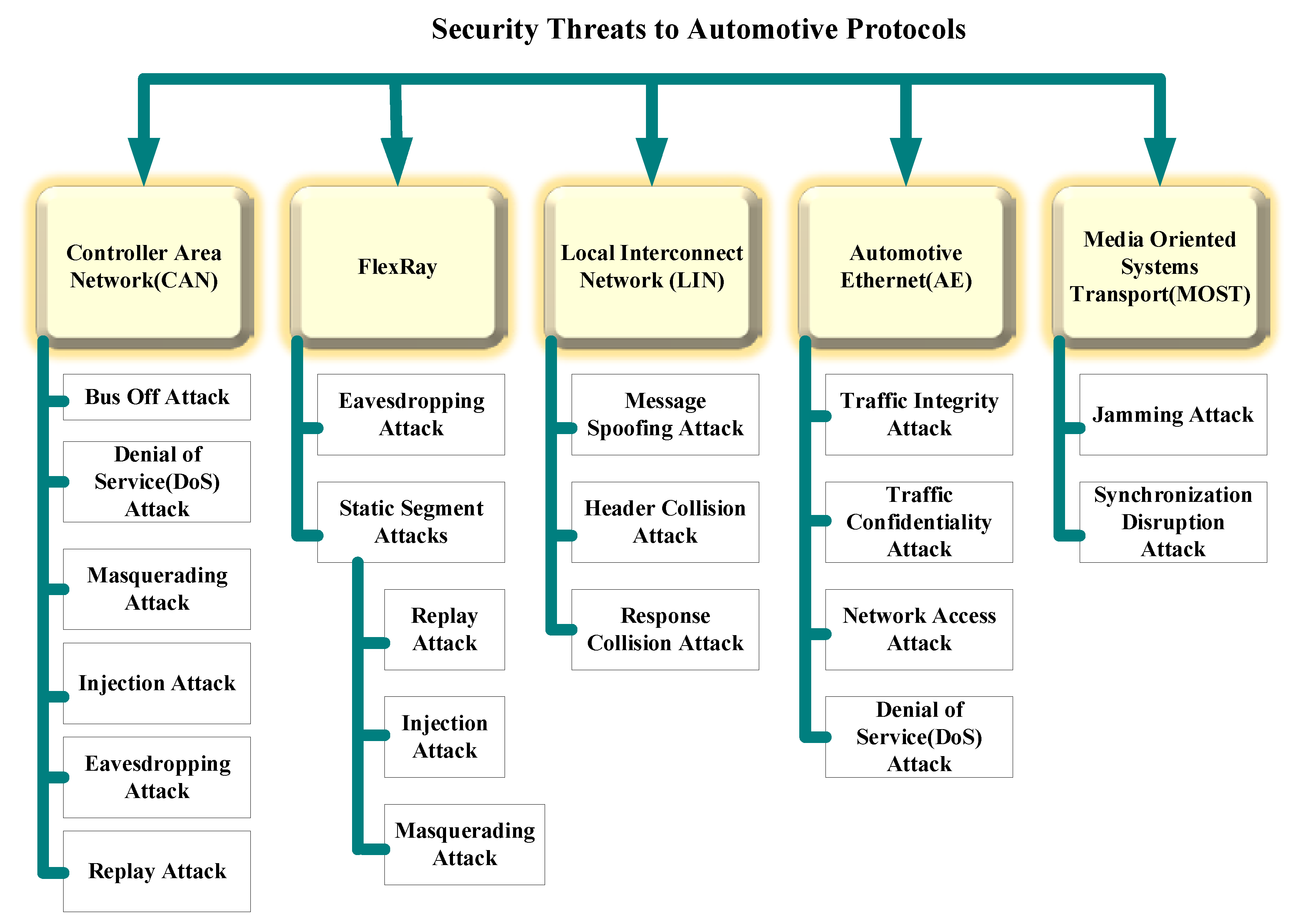
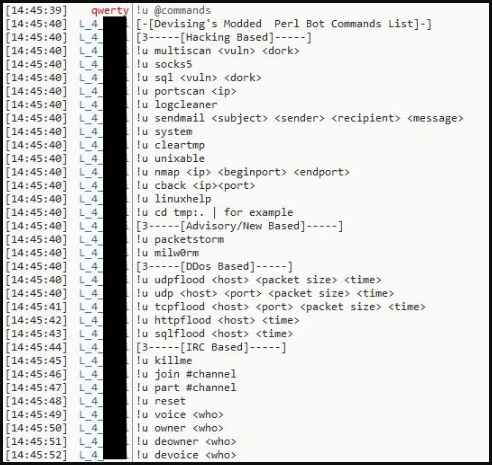
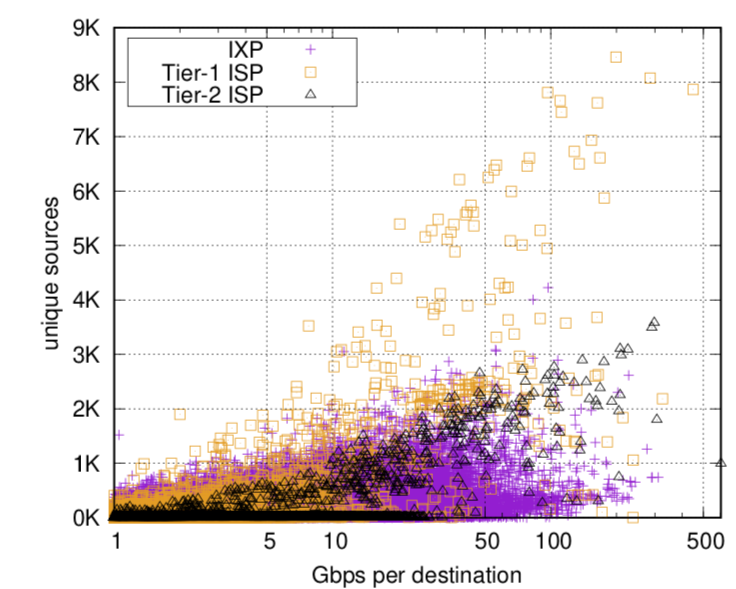
Machine Learning Based Approach for Detecting Distributed Denial of Service Attack by Qozeem Adeniyi Adeshina A project report s
Machine Learning Based Approach for Detecting Distributed Denial of Service Attack by Qozeem Adeniyi Adeshina A project report s
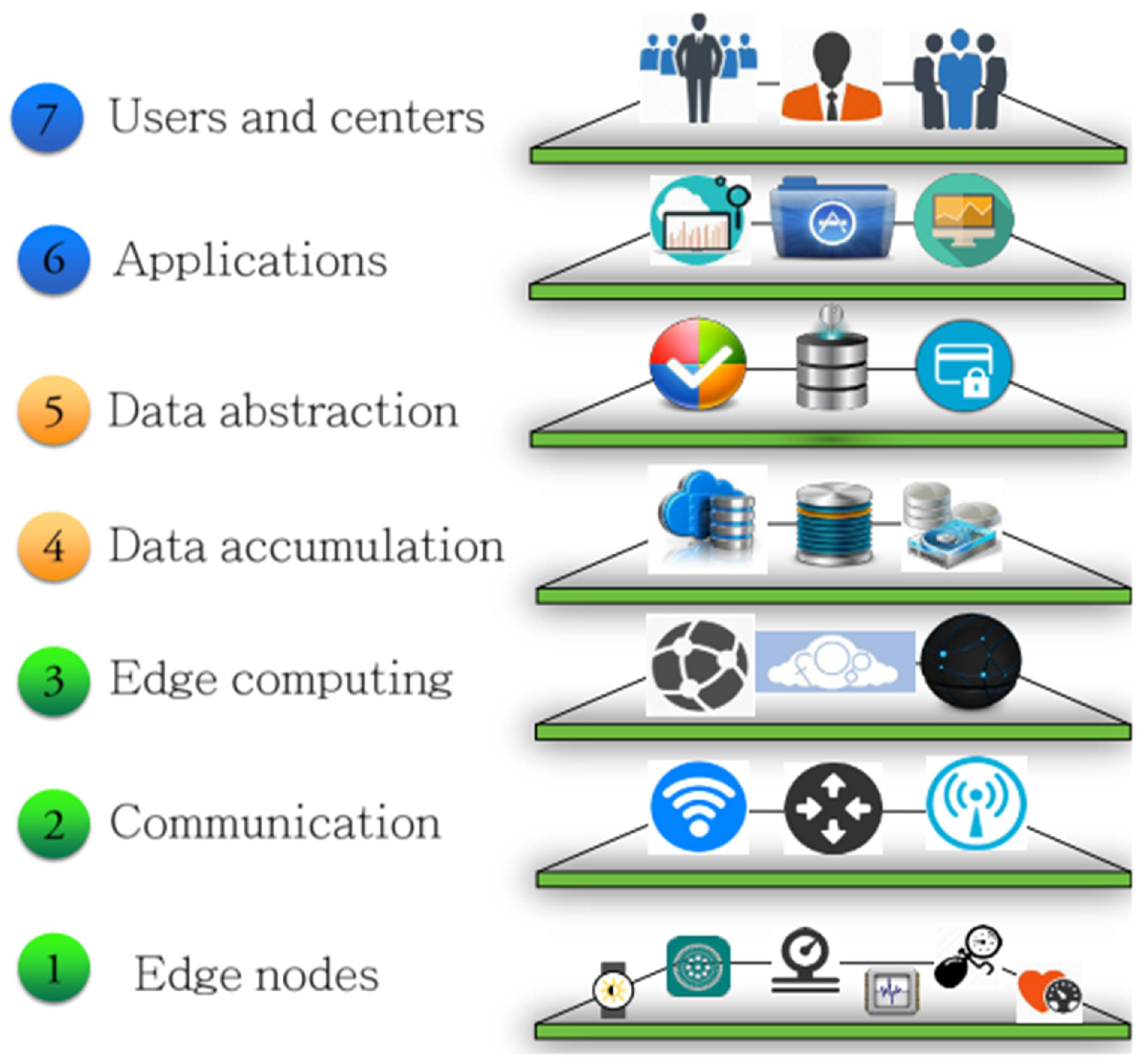
JSAN | Free Full-Text | A Comprehensive Study of Security and Privacy Guidelines, Threats, and Countermeasures: An IoT Perspective

PDF) IoDDoS — The Internet of Distributed Denial of Service Attacks: A Case Study of the Mirai Malware and IoT-Based Botnets


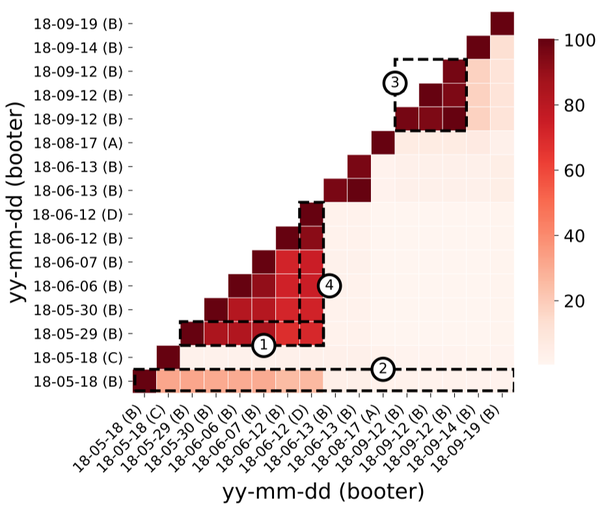

![TUTO] Comment trouver l'ip de quelqu'un sur skype et le BOOT (DDOS) - YouTube TUTO] Comment trouver l'ip de quelqu'un sur skype et le BOOT (DDOS) - YouTube](https://i.ytimg.com/vi/iwYldG8VYsY/maxresdefault.jpg)